That’s the bad news. The good news is that with just a few simple steps, you can easily learn to recognize the most common attacks and protect yourself accordingly.
Personalized Extortion
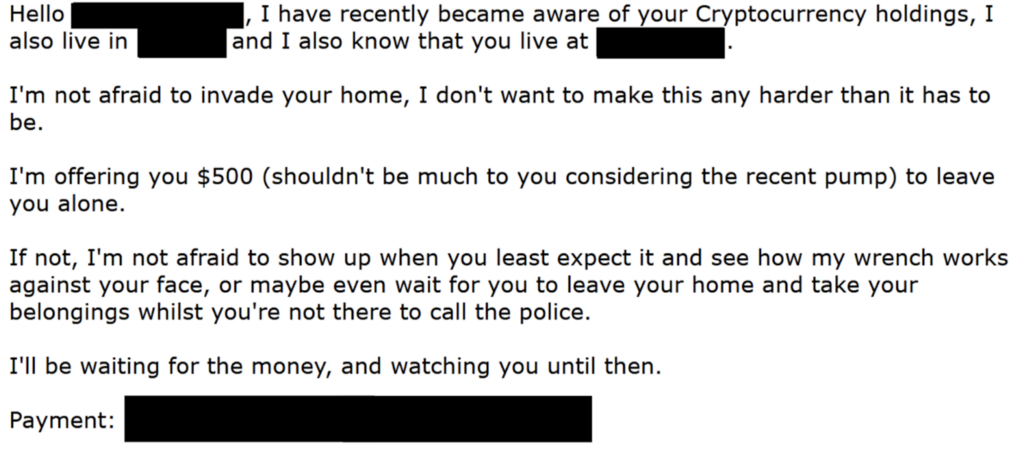
Receiving an email like this can be pretty terrifying — which is precisely the goal of the attacker. Fear, shame, or embarrassment are common tactics used by extortionists to coerce their victims into paying funds, even when there’s no actual security risk.
While everyone’s personal circumstances are different, our general advice is to completely ignore messages like this. Most extortionists are looking for easy targets, and will generally move on if they don’t receive a response. Of course, if you do have concerns for your personal safety or receive escalated extortion attempts, you should contact local law enforcement immediately.
Ledger Impersonation
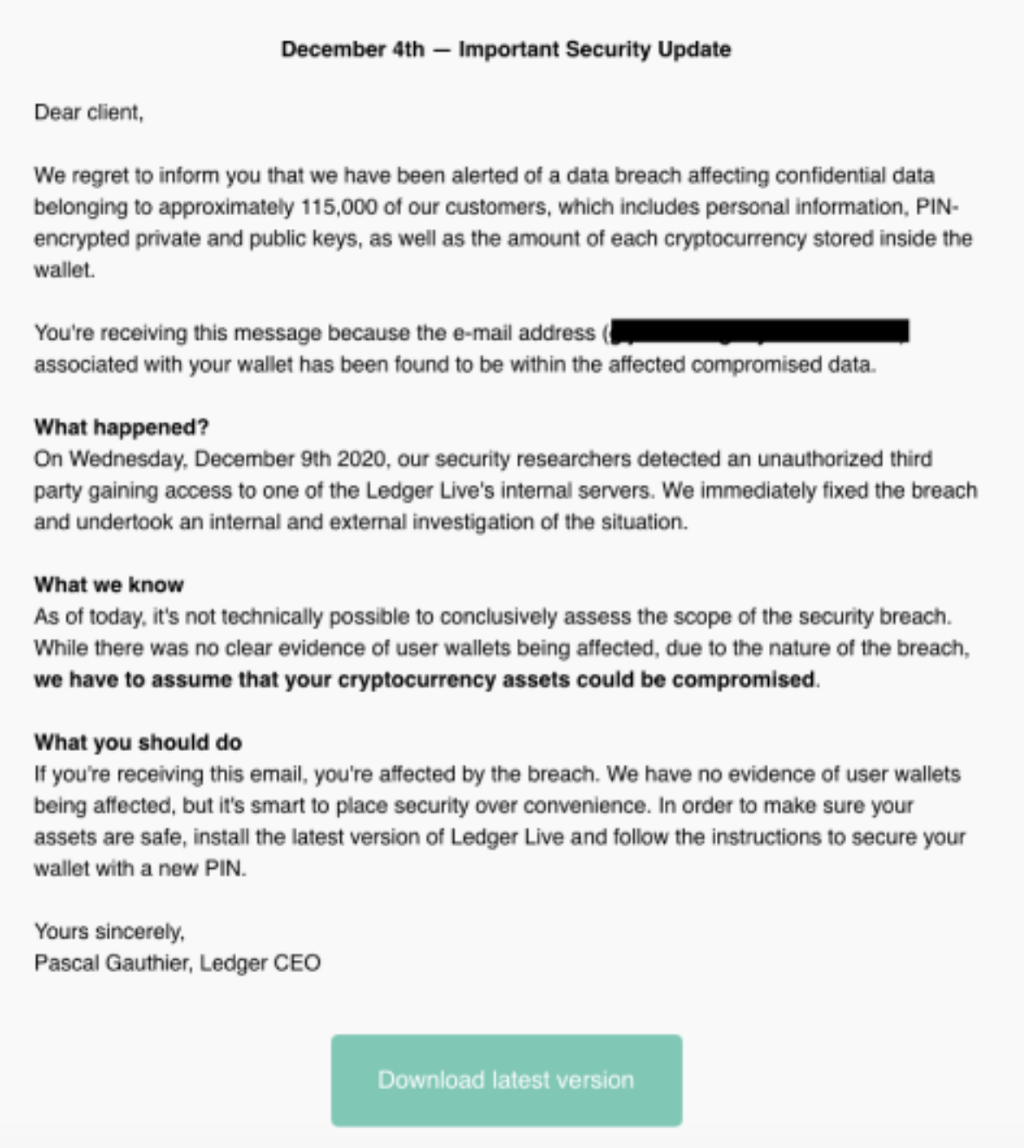
At first glance (and even at second glance), this email looks plausible, and it’s not easy to discern the fact that it is designed to fool you into downloading malware that will steal your cryptocurrency private keys.
As a general rule of thumb, if an email is asking you to do something that you’re not expecting or didn’t request, you should treat it with caution. Some phishing links and websites can look very realistic, so if you have any doubts about its authenticity, it’s better to visit the website directly by typing in the URL, or finding the top non-advertisement search result in any major search engine (yes, scammers abuse search engine ads too!)
If you receive an email claiming to be from Coinbase and you’re not sure whether it’s authentic, you can forward it to [email protected] for verification.
SIM-Swaps and Other Attacks
Even if you don’t receive any phishing emails or extortion attempts resulting from the Ledger breach, the exposure of your personal information does put you at risk for other attacks, including SIM-swaps and increased targeting of your other exchange accounts and cryptocurrency holdings.
To help keep your Coinbase account(s) secure, we strongly recommend implementing the following steps:
Be on the lookout for targeted phishing emails claiming to be Coinbase. Please see our help article for more information about recognizing Coinbase-related phishing attempts.
Check your email at haveibeenpwned.com* or a similar third-party data breach monitoring site and ensure that you’re using strong, unique passwords for any account or email address that has been exposed in a previous breach.
Enable the strongest form of 2-step verification available to you for both your Coinbase account and your email. Please see our 2-step verification help article for available options.
Set up a Vault Wallet to securely store your long-term holdings.
Check your Coinbase and email activity history often for any events that you do not recognize.
Additional security tips:
Create a strong unique and complex password for your email and Coinbase accounts (use a password that is long and random, stored in a password manager like 1Password or LastPass.)
Contact your mobile carrier and ask them about additional security measures you can put in place for your mobile device.
Regularly update your browser, phone, and computer to the latest versions to ensure you have applied all available security patches.
Read our security tips and best practices help article.
As a reminder, Coinbase Support will never call you directly, ask for remote access to your computer, ask you to send digital currency to an external address or ask for your security codes and passwords.
If at any time you believe your Coinbase account was compromised, see our account compromise help article to disable your account.
*This is a third-party website.
was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.

